Page Summary
-
Google is increasing transparency for Android System SafetyCore and Android System Key Verifier APKs through a transparency log.
-
Android System SafetyCore provides privacy-preserving on-device user protection infrastructure for apps.
-
Android System Key Verifier is a service for contact verification on Android, allowing users to confirm they are communicating with the intended person.
-
The transparency log contains entries for new versions of these APKs, including the hash of the code signature, hash type, package name, and version number.
-
The transparency system helps detect and deter supply chain attacks by allowing users to verify APK authenticity against the log.
As part of Google's continuous investment in transparency of its products, we are adding transparency to two new Google system services APKs: Android System SafetyCore (com.google.android.safetycore) and Android System Key Verifier (com.google.android.contactkeys). These APKs power the Sensitive Content Warnings and cryptographic key verification feature in Google Messages respectively. The transparency log we published to verify the claims that we make with regards to these APKs.
In light of advancements in AI, we are also now adding transparency to the following APKs:
- Private Compute Services (com.google.android.as.oss)
Covered Packages
This section describes packages that are covered in the transparency log and also their respective code transparency signing keys.
Android System SafetyCore
Android System SafetyCore (com.google.android.safetycore) is an Android system component that provides privacy-preserving on-device user protection infrastructure for apps.
Code from this APK is currently signed with the following key described by this certificate:
-----BEGIN CERTIFICATE-----
MIIFyDCCA7CgAwIBAgIUf3otg1DSj4EfxlP2OjAapoQ/moEwDQYJKoZIhvcNAQELBQAwdDELMAkG
A1UEBhMCVVMxEzARBgNVBAgTCkNhbGlmb3JuaWExFjAUBgNVBAcTDU1vdW50YWluIFZpZXcxFDAS
BgNVBAoTC0dvb2dsZSBJbmMuMRAwDgYDVQQLEwdBbmRyb2lkMRAwDgYDVQQDEwdBbmRyb2lkMCAX
DTI0MDcxNzIwNDQzMFoYDzIwNTQwNzE3MjA0NDMwWjB0MQswCQYDVQQGEwJVUzETMBEGA1UECBMK
Q2FsaWZvcm5pYTEWMBQGA1UEBxMNTW91bnRhaW4gVmlldzEUMBIGA1UEChMLR29vZ2xlIEluYy4x
EDAOBgNVBAsTB0FuZHJvaWQxEDAOBgNVBAMTB0FuZHJvaWQwggIiMA0GCSqGSIb3DQEBAQUAA4IC
DwAwggIKAoICAQCw93tMu9bD3tAfP1XDj2Y/vvBqDTvi86HesUK8gq0M7kxttep0BP2AkZS5AdVa
DNW6kuMhUN1XOao/Ib/mpgdi3pK6w0WDIlpHsg3coRuCxeniROw3+XUSLNox1mqfLSgHNg9gNoxK
dUyGf8nEIYVgLBUH8OX2oKeirRT7DyR64uVJmts0B0RvNt5VfP5vf6KFpa0prqCNGqQLHLyev3g/
35RH1oAVVsjZnylDYAm9qdAVugL0sgExY01vRNluZZKJuItNpdt+AMOTgStZAEwkhAg7pMbNF27g
AJDCC+XDS16/x1Jnxc+Exlw66aHB++1+dFK/rYkbB+ql4dHjs/LTGqPIeUuE3Xd7UkguKZRRLNtI
Ls9DP1UYuQGZ1IQ9kQamkxScNFgNmymkgTXhBajDKSPy4jb2t5yLHTIJn0OvyMLg2J7/ImHHmc99
07OuXCfy55aW99lqaYsc+rLPOHFi6GjvTUkkyxXqJlhQYb9uQznxkqsfbnBefxCCO924uVIwWDlt
rA+mQ3Bw7TNgb3NmKUmUrmFaRBmrAxnag/jj0N4ff7vXVBR0WkXpb3qRPlSvsEXGYOWPJtc2+U2Q
IFcNyEeu6zWD5yYIcnoX1go2zEVt99b1AFsN0zRWo0mNyeLizDNiDkGT9AtB8rdajhchDqfmZGGX
XqhhJVT9IRMBFQIDAQABo1AwTjAMBgNVHRMEBTADAQH/MB0GA1UdDgQWBBQY4GYL4FxVcxk2Euj8
otSQHVYz7zAfBgNVHSMEGDAWgBQY4GYL4FxVcxk2Euj8otSQHVYz7zANBgkqhkiG9w0BAQsFAAOC
AgEAoDuItwszr0yIPcvn/l3s5xZs+3rXe52KcY+ZgMVyM4q5CTEHwX89+K+hMFMTqp8vkrLhjnhz
/SYEY0ZXMQsQ0GWrMHbfIbzUsLhIoMBYn1JA+AH+CCZIYo9GbxaCqu4KJPQNC7sqA3goWf6UqHya
rj8wzXT5+qmOVwBUHgQUap5406/DaPqU0g+w4+hiV/zI67ugWU1z+6WElYIsXjN59zA5rVIJTdnV
w04RNK5fldWUsbkPGQ7hwoyJG4wZewCZ0sU4NUqVecb8z52hdlGj15+rUhDJq0pbDRjFEnulfUFJ
gA5s6iosSYyXrGQgE6NOszxu7nMvSg7MPrS7GQUMnaadQAye/7ELBY4jxlHMOAuj9iwz2Asjuy0a
ye64nfcYBbFSIzV7xRgeUJy42jyRq9ZoILU9fW/I4rHNIcntgB2POpzFOZrKXLC/B8rHKZT9AZOd
iXEKqFRBnHEaGy+MARO7guCQLO8XIVQixDHWS6OJRIvw0LKaf4dSlCxcUEpYSSHJmt6JMOujapCa
JmKz7K+wZWSClJnrc0HhJnZFt6S3TakZx7ALVi0SqxBaxHYFieSn9rmXHOWrSxEz5cmASnsfqnc0
w//Yhjm+gGOmLs/5TzrCyYvYt8Ynsd1G1GHipwc8JXGxLqbOPrNcUpjM65m+sshERIua30du0GOm
4ZM=
-----END CERTIFICATE-----
Android System Key Verifier
The Android System Key Verifier APK (com.google.android.contactkeys) is a service for contact verification on Android. It allows a user to verify a contact's public keys to confirm they are communicating with the person they intend to message. The service is a unified system for public key verification across different apps, which uses verification through QR Code scanning or number comparison.
Code from this APK is currently signed with the following key described by this certificate:
-----BEGIN CERTIFICATE-----
MIIFyDCCA7CgAwIBAgIUQwApn2X0vcGMw/VyRoUQkFXuekYwDQYJKoZIhvcNAQELBQAwdDELMAkG
A1UEBhMCVVMxEzARBgNVBAgTCkNhbGlmb3JuaWExFjAUBgNVBAcTDU1vdW50YWluIFZpZXcxFDAS
BgNVBAoTC0dvb2dsZSBJbmMuMRAwDgYDVQQLEwdBbmRyb2lkMRAwDgYDVQQDEwdBbmRyb2lkMCAX
DTI0MDczMTE5MzY0MVoYDzIwNTQwNzMxMTkzNjQxWjB0MQswCQYDVQQGEwJVUzETMBEGA1UECBMK
Q2FsaWZvcm5pYTEWMBQGA1UEBxMNTW91bnRhaW4gVmlldzEUMBIGA1UEChMLR29vZ2xlIEluYy4x
EDAOBgNVBAsTB0FuZHJvaWQxEDAOBgNVBAMTB0FuZHJvaWQwggIiMA0GCSqGSIb3DQEBAQUAA4IC
DwAwggIKAoICAQDKZqLKu5eeBir6muCiQ5vGQxIDzZcQhLZLpbAkVBNKcrpjgMB6ef0JvrKBnmzN
tHzgExjv4jzyZ1UnU8kaTinVWZF5F9unwuH/957zpc9Ja/JDioGn0V0Q4fgCfIaCLxj4GxK9ywby
TMBWg4ZN0nzcNTCX7ygSzZa24qSq/zOJd2wcO6RxO6MOS2TJPBABA1Wi6l7R/ldXDvzy/3doy5VU
4SElcwWosLFr4jORKGK4R0en96722skXCfl3kNz0J/aIUohdd3cggRnUX7N7tz1nlJpKmDFKeuKn
4lTITUf0MKWzs6PKabyoHzJZYf3XNN88cDy41wR9lsA33DSutuS2tQ2wUlXHfzikZVoI/kCANLW1
2ew3Wo+1D/qYhWXDzO8eM/c4R17vpzSt3kl/2IkYVuHvp1S4luY0DT3S9rKYg630BO+ubEg5NaMt
hGpCAcfMu8WUbdpWxIvdHPM8mQZbzSB2r5eON7ufzq3pB9pwKvslpdNtINvrKtZCrMSqTTqVI2dL
8d8YWIFHYySgKZFKNNcG0Y/OapbAy8zoQZT8oz4P0lWCTVcCoh/54jCBdAKUO+LOm3ATMzw/v57o
g1Lr0wTM7YjFkToGI/dytMyEFkG3fGxYcgzkn3pu0EoQ4FsrnL3jHcIKPCX6wSykXzODVwPLoO3z
YQHn1i0dxzIkKwIDAQABo1AwTjAMBgNVHRMEBTADAQH/MB0GA1UdDgQWBBQU/Oocht8Ntbcrqvx5
xljCPmYp1DAfBgNVHSMEGDAWgBQU/Oocht8Ntbcrqvx5xljCPmYp1DANBgkqhkiG9w0BAQsFAAOC
AgEAaWxz1VV1hUE+A/rQZNfNe2IH1B9f+4QCSF/VRmEOfSUB346cZgtSMkGpirXOczu0FExUAWzc
9GDV+w59P0YZ37IgB9l8nFh6qW9oCTBp3IOitvfKrz4x6GDhx6iU4j7WU60ezQZKnnchh4fIvraA
vy3m6/PLr6cbIvlHsUqCtt0gbNyj+fAgxJtbDSkqMwxYBOaOhQYQepkQuYD+juO08knwzMy5yFPL
MWBuhdB9Mqvv3l1MNcOB1Y+8RJGTp66ft1pVE2zuBDgix8m/Hizuewlws5xzLap/Rcx2BCHIFBlW
k4VbSZ6ERtkb/uh/q30psrBxcROxDR1LbynvPsayC+0pUjXCMVD7de3+HkeKiAT+OPQf8EAx2bMx
Nyz858lpVX9Eh92Q5jE/sxLvij3T6rBUBdatfpuE1dxGlpHNL7NVOEQpDOCZi9jSPstAoKYdtEzk
Im85maujM8udLoexXBTLgwYc/9Zz0nJXuVQJYyon70thXTrBc43gmi646rU4YFFhIei9N4dUQNgO
fxCGd8y8L8fTFAWQm9YQ7x7uxwjkalCh/ahRDtCdyk/ab8mHl/V1M5gkylUW6lt0Ba8Yw6j8PWqc
+io39beMlVWMfwj5mO2MTIKmUChUxULvQPcR46hve5mhSVZeBohPWnrc6B5XTf/4siWWRu0rYBD8
PLM=
-----END CERTIFICATE-----
Private Compute Services
The Private Compute Services APK (com.google.android.as.oss) is a system service that enforces privacy protections for user data that is used by AI-driven features on an Android-powered device. Private Compute Services acts as a secure and auditable gateway for Private Compute Core (PCC) applications like Android System Intelligence (AiAi), which handle sensitive on-device data, to access network resources. By providing well-defined, privacy-first APIs for tasks such as HTTP downloads and federated learning, and by making its code publicly available, Astrea allows users and researchers to verify that data is being handled in a privacy-preserving manner.
Code from this APK is currently signed with the following key described by this certificate:
-----BEGIN CERTIFICATE-----
MIIFyDCCA7CgAwIBAgIUPIfmnXD2AYeVSlyU47VpvrSddBYwDQYJKoZIhvcNAQELBQAwdDELMAkG
A1UEBhMCVVMxEzARBgNVBAgTCkNhbGlmb3JuaWExFjAUBgNVBAcTDU1vdW50YWluIFZpZXcxFDAS
BgNVBAoTC0dvb2dsZSBJbmMuMRAwDgYDVQQLEwdBbmRyb2lkMRAwDgYDVQQDEwdBbmRyb2lkMCAX
DTIwMTEwMjE2NDYxMFoYDzIwNTAxMTAyMTY0NjEwWjB0MQswCQYDVQQGEwJVUzETMBEGA1UECBMK
Q2FsaWZvcm5pYTEWMBQGA1UEBxMNTW91bnRhaW4gVmlldzEUMBIGA1UEChMLR29vZ2xlIEluYy4x
EDAOBgNVBAsTB0FuZHJvaWQxEDAOBgNVBAMTB0FuZHJvaWQwggIiMA0GCSqGSIb3DQEBAQUAA4IC
DwAwggIKAoICAQCo3fIiBMXusWZ08FYKRgvgwSELjnUaf/F7D5EwsDmVDRbetIb10S8o/Utk09Nu
5peG1ayrtVyYXV3vHEi6T/3VFniAnaRMOsBT0DsMilTzgTemZcelEMx6wr2TOH0jLtnrgNdcikfW
gmEv3ierkxVuT23fckwyjk5R9nNJkU7s3lLTVFnjRFt+Z5xFFYRrWVqLgS5RObvHMwbggmoTMUcv
cTFPEMKrZPmF8jJeg9JP4U28sL3Hk+eh3fwoVuahBfYnObHWR/bxqNvIsR1tH918cy7pNtfWfgdT
QQxOVz+xPYOv6AHh6CNwHWM2dhQH6EmIwyXdG3D/GKcde1OUrQp5C/F+ToD4rw+LMP0WCW//RIsR
mvCZKvPiii2lEJQh/+akwwUbovhXey6iGC9HYCQYxyYztu2LAkAEV2s5nLPgrV2s65AROy4qd3Bk
NxKgabqwls0Ho66Lb3OGbLNBcx7YOa/gA+AzwocftsJGPLcQCTf0R7eeDGbRnkJF8OihmU8kQ9L/
K/oLPhAyix197rzmsJyMn0M0e2l1ZhWFSrTVkW7mTbq2F8hHqBNkSQwRkHJqYp7Bpwgw9eo3HuJ/
cXZQMVFWZYPMIEJ4A4qhTAhR5MjhWm0NE/v+MjyDLqri9oNC4MlldbHp5qivufz61FNrSADSViub
DGjfrzxeqNOukwIDAQABo1AwTjAMBgNVHRMEBTADAQH/MB0GA1UdDgQWBBTNbZUz0f2Sk7M+FVHq
3n9q0zceWTAfBgNVHSMEGDAWgBTNbZUz0f2Sk7M+FVHq3n9q0zceWTANBgkqhkiG9w0BAQsFAAOC
AgEAgZg6oZVgXN1yU3Uc92NH/BnkSOkMwJzKFD9wyiHnjruGLl0pOa4C4cJDMvyfdg2BYDVmWLF+
Sx8z9KZH3ghfC5QVTaZARyS5k9rAOfpEndGXBHGZEcUYi1MHeRpsdeW2xxv6WtOgS53QaAd1PjF3
SFiKwspfVdjDIHiiAmCydCcKagqDvdvsQueAzHAZVOMTzKHfYaSLA5KkJF753SRuh4JnUAvbasYA
AdyDYe85ZS5/g6+3kF0bERA2226Rrm8r2QgLhn6lSq9G3Db69oqO2zIUdcBNsog9IBnTUrs9VRrY
9kz793vM9DM1RjEng454XXKg6MUB3xv2xchPBsLcZcn9pyoUhCiCObuawLB2IxnuHBfsAwqge5pX
EKND3jW3d3RBHYGu5EVBVk2nxc1EzJfO1uFk1AWaLMhWZMw49QIvp9PljJ57TB/6H1REtkxbhIDP
cf/JWMx6ugaPod75mJHiQLmBCJ1OcUMOKBsX5heB3GwVma28/wjraMb/30xsGKUHtNVm5r+TykKs
r56j6FXw3DTmcbNTKZ926Z6+GzkBhY87mY3PLzFBtkAV8kGcXUgBOrXPHiVsBPLq3N3rM2pjfsMu
d7chNImj0JZvQ0xRieCyp31fy9BaFxdXesTw7xg7lRjHQ9ZVRqnbAwVdAQGFbRp9ndOkTr7i+xzC
asY=
-----END CERTIFICATE-----
Threat Model
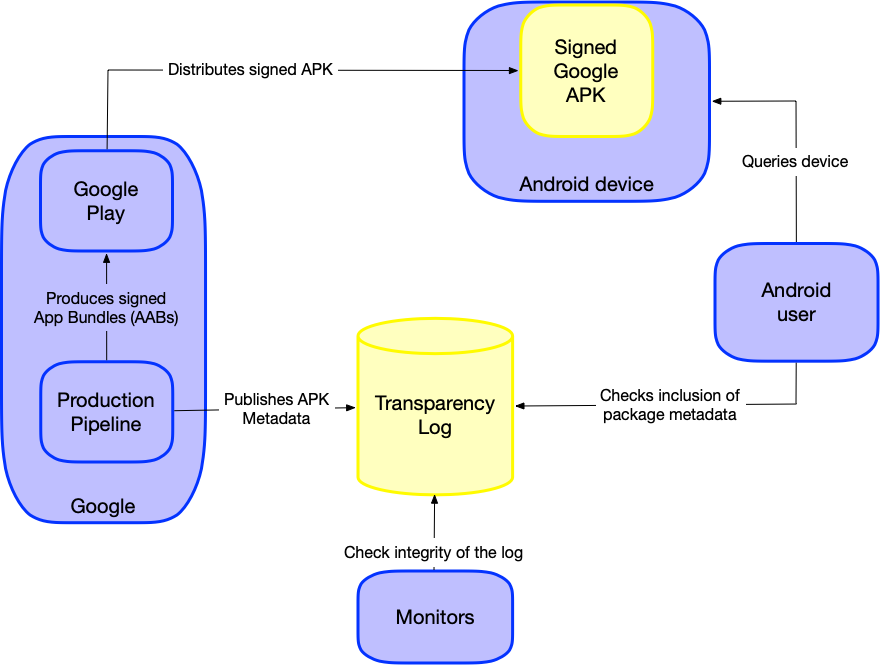
Transparency systems can be used to detect - and thus deter supply chain attacks. We illustrate with some examples.
Suppose an attacker maliciously modifies a Google system services APK and even manages to sign it with the signing key that is used by Google Play. Anyone who receives the malicious APK can query the binary transparency log to verify the APK's authenticity. They will find that Google has not added the corresponding APK metadata to the log and will know not to trust the compromised APK.
Since publishing to the log is a separate process from the release process with signing (as illustrated in the Ecosystem Diagram), this raises the bar for the attacker beyond just compromising the key.
While we plan to also integrate this log into a public network of witnesses using a standard witness protocol, we encourage external, independent parties to monitor the integrity of this publicly available log. These parties can attest to the append-only property of the log, and report any tampering.
The existence of such a transparency system and the additional discoverability of attacks discourages malicious activity. If an APK is compromised but users only trust those that are in the log, the compromised APK would need to be publicly exposed. This increases the likelihood of discovering that the compromised APK exists, and action can be taken to remove its distribution.
Claimant Model
The Claimant Model is a framework used to define roles and artifacts in a verifiable system. In the case of Google System Services APK Transparency, the claim we make is that the hash of signed binaries recorded in this log represents official code for respective Google system services APKs.
- ClaimGoogleSystemServicesApk: (I, Google, claim that
$codeSignatureis for$googleSystemServicesApk), where:$codeSignatureis a signed JSON Web Token (JWT) that contains a list of DEX files and native libraries and their corresponding hashes included in a specific version of$googleSystemServicesApk.$googleSystemServicesApkis an Android package (APK) from the following set of packages:{Android System SafetyCore (com.google.android.safetycore), Android System Key Verifier (com.google.android.contactkeys)}
Anyone who has a copy of $googleSystemServicesApk can verify the claim above,
and we describe this process in full detail in the verification page.
Log Content
When Google releases a new version of the APKs listed above, it adds a corresponding entry to the Google System Services APK Transparency Log.
Each entry in this log contains four pieces of APK metadata:
- The hash of the code signature of a Google developed APK. This is a hex string of the SHA256 digest of a code transparency token (also known as Code Transparency JWT).
- The description of the type of hash above. This is a string.
- The package name of the APK. This is a string.
- The version number (versionCode) of the APK. This is an integer.
The format of a log entry is the concatenation of the four pieces of
information with a newline (\n) character, as illustrated by the following:
hash\nSHA256(Signed Code Transparency JWT)\npackage_name\npackage_version\n
Note that in this release, we are experimenting with utilizing
code transparency.
This means that instead of the hash of the APK, we are recording the digest of
the code transparency token.
Thus the hash description is currently fixed as
SHA256(Signed Code Transparency JWT).
Additionally, this demonstrates a way code transparency can be utilized by app developers when their app signing keys are held by Google Play.
Ecosystem Diagram