You can assign static external IP addresses to your virtual machine (VM) instances. You can also change, list, and release static IP addresses for your VMs. To reserve a static external IP address, see Reserve a static external IP address.
External IP addresses can be static or ephemeral. If a VM requires a fixed external IP address that does not change, do the following:
- Obtain a static external IP address. You can reserve new external IP addresses or promote existing ephemeral external IP addresses.
- Assign the reserved IP address to an existing VM, or assign it when creating a new VM.
If you require a static IP address on your internal Compute Engine network, see Reserve a static internal IP address instead.
Before you begin
- Read about IP addresses.
- Read about quotas and limits for static external IP addresses.
- Read about external IP address pricing.
-
If you haven't already, set up authentication.
Authentication is
the process by which your identity is verified for access to Google Cloud services and APIs.
To run code or samples from a local development environment, you can authenticate to
Compute Engine as follows.
Select the tab for how you plan to use the samples on this page:
Console
When you use the Google Cloud console to access Google Cloud services and APIs, you don't need to set up authentication.
gcloud
-
Install the Google Cloud CLI, then initialize it by running the following command:
gcloud init
- Set a default region and zone.
Terraform
To use the Terraform samples on this page from a local development environment, install and initialize the gcloud CLI, and then set up Application Default Credentials with your user credentials.
- Install the Google Cloud CLI.
-
To initialize the gcloud CLI, run the following command:
gcloud init
-
Create local authentication credentials for your Google Account:
gcloud auth application-default login
For more information, see Set up authentication for a local development environment.
REST
To use the REST API samples on this page in a local development environment, you use the credentials you provide to the gcloud CLI.
Install the Google Cloud CLI, then initialize it by running the following command:
gcloud init
-
Required roles
To get the permissions that you need to configure and manage static IP addresses, ask your administrator to grant you the following IAM roles on your project:
-
To create and update VMs:
Compute Instance Admin (v1) (
roles/compute.instanceAdmin.v1)
For more information about granting roles, see Manage access.
These predefined roles contain the permissions required to configure and manage static IP addresses. To see the exact permissions that are required, expand the Required permissions section:
Required permissions
The following permissions are required to configure and manage static IP addresses:
-
compute.instances.updateon the VM instance -
compute.instances.updateNetworkInterfaceon the VM instance -
compute.instances.addAccessConfigon the VM instance -
compute.instances.deleteAccessConfigon the VM instance -
compute.networks.liston the network -
compute.subnetworks.useon the subnet -
compute.subnetworks.liston the subnet -
To create VMs:
compute.instances.createon the project- To use a custom image to create the VM:
compute.images.useReadOnlyon the image - To use a snapshot to create the VM:
compute.snapshots.useReadOnlyon the snapshot - To use an instance template to create the VM:
compute.instanceTemplates.useReadOnlyon the instance template - To assign a legacy network to the VM:
compute.networks.useon the project - To specify a static IP address for the VM:
compute.addresses.useon the project - To assign an external IP address to the VM when using a legacy network:
compute.networks.useExternalIpon the project - To specify a subnet for the VM:
compute.subnetworks.useon the project or on the chosen subnet - To assign an external IP address to the VM when using a VPC network:
compute.subnetworks.useExternalIpon the project or on the chosen subnet - To set VM instance metadata for the VM:
compute.instances.setMetadataon the project - To set tags for the VM:
compute.instances.setTagson the VM - To set labels for the VM:
compute.instances.setLabelson the VM - To set a service account for the VM to use:
compute.instances.setServiceAccounton the VM - To create a new disk for the VM:
compute.disks.createon the project - To attach an existing disk in read-only or read-write mode:
compute.disks.useon the disk - To attach an existing disk in read-only mode:
compute.disks.useReadOnlyon the disk
You might also be able to get these permissions with custom roles or other predefined roles.
Limitations
Only one resource at a time can use a static external IP address.
There is no way to check whether an IP address is static or ephemeral after it has been assigned to a resource. You can compare the IP address against the list of static external IP addresses reserved to that project. Use the
gcloud compute addresses listsub-command to see a list of static external IP addresses available to the project.Each VM can have multiple network interfaces, and each interface can have the following IP addresses assigned:
- An internal IPv4 address (required)
- An external IPv4 address
- A
/96IPv6 address range, either internal or external, but not both
You cannot change the name of a static IP address.
Assigned external IP addresses exist on the same physical host as the VM and exist in the same region as the VM for all purposes, including routing, latency, and pricing. This is true regardless of internet geolocation lookup information.
Note: Network interfaces can receive traffic from
multiple
forwarding rules, which might serve other external IP addresses. Any
number of external IP addresses can reference a network interface through
these forwarding rules, but each network interface can be assigned only one
external IPv4 address and one external /96 IPv6 address range.
For more information about load balancing and forwarding rules, read the load balancing documentation.
View available static external IP addresses
To list static external IP addresses that you have reserved for your project, follow these steps.
Console
In the Google Cloud console, go to the IP addresses page.
Click External IP addresses.
gcloud
Use the gcloud compute addresses list command:
To list all IP addresses, use the following command:
gcloud compute addresses list
To list all global IP addresses, use the following command:
gcloud compute addresses list --global
To list all regional IP addresses in a given region, use the following command:
gcloud compute addresses list \ --regions=REGIONReplace
REGIONwith the region that you want to list addresses for. You can list addresses of multiple regions by specifying comma-separated region names:gcloud compute addresses list \ --regions=REGION1,REGION2,..REGION_n_
API
To list regional IPv4 or IPv6 addresses, call the
addresses.listmethod:GET https://compute.googleapis.com/compute/v1/projects/PROJECT_ID/regions/REGION/addresses
Replace the following:
PROJECT_ID: the project ID for this requestREGION: the name of the region for this request
To list all addresses in all regions, call the
addresses.aggregatedListmethod:GET https://compute.googleapis.com/compute/v1/projects/PROJECT_ID/aggregated/addresses
To list global IPv4 or IPv6 addresses, call the
globalAddresses.listmethod:GET https://compute.googleapis.com/compute/v1/projects/PROJECT_ID/global/addresses
Replace the following:
PROJECT_ID: the project ID for this request
Configure static external IP addresses
The following sections describe how to configure static external IP addresses for your VMs.
Create a VM that uses a static external IP address
After you have reserved a static external IP address, you can assign it to a VM.
Console
In the Google Cloud console, go to the Create an instance page.
Specify the VM details.
Expand the Advanced options section.
Expand the Networking section.
In the Network interfaces section, expand a network interface to edit it.
To assign an IPv4 address, do the following:
- Select a network.
- Select the IP address from the External IPv4 address list.
To assign an IPv6 address, do the following:
- Select a network that contains an IPv6 subnet.
- Select a dual-stack subnet from the Subnetwork list.
- For IP stack type, select IPv4 and IPv6 (dual-stack).
- Select the newly reserved external IPv6 address from the External IPv6 address list. Alternatively, select CREATE IP ADDRESS and reserve a new static external IPv6 address.
- For Network Service Tier, select Premium.
To finish modifying the default network interface, click Done.
Continue with the VM creation process.
gcloud
You can create a VM and assign a static regional external IP address that you have already reserved.
To assign a static external IPv4 address, do the following:
gcloud compute instances create VM_NAME --address=IP_ADDRESS
Replace the following:
VM_NAME: the name of the VM.IP_ADDRESS: the IP address to assign to the VM. Use the reserved static external IP address, not the address name.
To assign a static external IPv6 address, do the following:
gcloud compute instances create VM_NAME \ --subnet=SUBNET \ --stack-type=IPV4_IPV6 \ --external-ipv6-address=IPV6_ADDRESS \ --external-ipv6-prefix-length=96 \ --ipv6-network-tier=PREMIUM \ --zone=ZONE
Terraform
You can use the google_compute_instance resource
to assign an external IP address.
REST
To assign a static external IPv4 address to a new VM, do the following:
In your request to
create a new VM,
explicitly provide the
networkInterfaces[].accessConfigs[].natIP
property and the external IPv4 address that you want to use. For example:
{
"name": "VM_NAME",
"machineType": "zones/ZONE/machineTypes/MACHINE_TYPE",
"networkInterfaces": [{
"accessConfigs": [{
"type": "ONE_TO_ONE_NAT",
"name": "External NAT",
"natIP": "IPV4_ADDRESS"
}],
"network": "global/networks/default"
}],
"disks": [{
"autoDelete": "true",
"boot": "true",
"type": "PERSISTENT",
"initializeParams": {
"sourceImage": "SOURCE_IMAGE"
}
}]
}
To assign a static external IPv6 address to a new VM, do the following:
In your request to
create a new VM,
explicitly provide the
networkInterfaces[].ipv6AccessConfigs[].externalIpv6
property and the external IPv6 address that you want to use. For example:
{
"name": "VM_NAME",
"machineType": "zones/ZONE/machineTypes/MACHINE_TYPE",
"networkInterfaces": [{
"accessConfigs": [{
"name": "external-nat",
"type": "ONE_TO_ONE_NAT"
}],
"ipv6AccessConfigs": [{
"externalIpv6": "IOV6_ADDRESS",
"externalIpv6PrefixLength": 96,
"name": "external-ipv6-access-config",
"networkTier": "PREMIUM",
"type": "DIRECT_IPV6"
}],
"stackType": "IPV4_IPV6",
"subnetwork":"SUBNETWORK
}],
"disks": [{
"autoDelete": "true",
"boot": "true",
"mode": "READ_WRITE",
"type": "PERSISTENT",
"initializeParams": {
"sourceImage": "SOURCE_IMAGE"
},
}],
}
Change or assign an external IP address to an existing VM
You can change or assign an external IP address, either ephemeral or static, to an existing VM.
A VM can have multiple interfaces and each interface can have an external IP address. If the VM already has an external IP address, you must remove that address first. Then, you can assign a new external IP address to the existing VM.
Console
- In the Google Cloud console, go to the VM instances page.
- Click the name of the VM that you want to assign an external IP to. The Instance details page displays.
From the Instance details page, complete the following steps:
- Click Edit.
- Expand Network interfaces.
- Select the required external IP address to assign to the VM:
- For External IPv4 address, select either Ephemeral or a static external IPv4 address.
- For External IPv6 address, select either Ephemeral or a static external IPv6 address.
- Click Done.
Click Save.
gcloud
Optional: Reserve a static external IP address.
If you want to assign a static external IP address, you must reserve an address and make sure that the address is not in use by another resource. If necessary, follow the instructions to reserve a new static external IP address or to unassign a static external IP address.
If you intend to use an ephemeral external IP address, you can skip this step, and Compute Engine randomly assigns an ephemeral external IP address.
Remove any existing IP address assignment, as described in Unassign a static external IP address.
Assign the new external IP address.
To assign an IPv4 address, use the
instances add-access-configsub-command:Note: Don't replaceIP_ADDRESSwith the name of the static IP address. You must use the actual IP address.gcloud compute instances add-access-config VM_NAME \ --access-config-name="ACCESS_CONFIG_NAME" --address=IP_ADDRESS
Replace the following:
VM_NAME: the name of the VM.ACCESS_CONFIG_NAME: the name to call this access config. Make sure to include the full name between quotes.IP_ADDRESS: the IP address to add.
If you want Compute Engine to assign an ephemeral external IP address rather than using a static external IP address, omit the
--address IP_ADDRESSproperty:gcloud compute instances add-access-config VM_NAME \ --access-config-name="ACCESS_CONFIG_NAME"
To assign an IPv6 address range, use the
instance network-interfaces updatesub-command:gcloud compute instances network-interfaces update VM_NAME \ --network-interface==NIC \ --ipv6-network-tier=PREMIUM \ --stack-type=IPV4_IPV6 \ --external-ipv6-address=IPV6_ADDRESS \ --external-ipv6-prefix-length=96 \ --zone=ZONE
Replace the following:
VM_NAME: the name of the VM.NIC: the name of the network interface.IPV6_ADDRESS: the IPv6 address to assign to the VM. Specify the first IPv6 address in the/96range.ZONE: the zone of the VM.
REST
You can change the external IPv4 or IPv6 address of a VM by adding a new access configuration for that VM.
Remove any existing IP address assignment, as described in Unassign a static external IP address.
Delete the existing access configuration by making a
POSTrequest to theinstances.deleteAccessConfigmethod.POST https://compute.googleapis.com/compute/v1/projects/PROJECT_ID/zones/ZONE/instances/VM_NAME/deleteAccessConfig
Add a new access configuration to the network interface of the VM by making a
POSTrequest to theinstances.addAccessConfigmethod.For IPv4 addresses, make the following request:
POST https://compute.googleapis.com/compute/v1/projects/PROJECT_ID/zones/ZONE/instances/VM_NAME/addAccessConfig { "natIP": "IPV4_ADDRESS", "name": "ACCESS_CONFIG_NAME" }For IPv6 addresses, update the
networkInterfaces[].ipv6AccessConfigs[].externalIpv6property and the external IPv6 address that you want to use.
Restrict external IP addresses to specific VMs
For certain workloads, you might have essential requirements that include security and network restrictions. For example, you might want to restrict external IP addresses so that only specific VMs can use them. This option can help to prevent data exfiltration or maintain network isolation. Using an Organization Policy, you can restrict external IP addresses to specific VMs with constraints to control use of external IP addresses for your VMs within an organization or a project.
The constraint for controlling external IP address on VMs is:
constraints/compute.vmExternalIpAccess
To use the constraint, you specify a policy with an allowedList of VMs that
can have external IP addresses. If you don't specify a policy, all external IP
addresses are allowed for all VMs. When the policy is in place, only the VMs
that are listed in the allowedValues list can be assigned an external IP
address, either ephemeral or static, and other Compute Engine VMs in
the organization or project that are not explicitly defined in the policy are
prohibited from using external IP addresses.
VMs are identified in the allow and deny lists using the VM's URI:
projects/PROJECT_ID/zones/ZONE/instances/VM_NAME
Specifications for restricting external IP addresses
- You can apply this list constraint only to VMs.
- You cannot apply the constraint retroactively. All VMs that have external IP addresses before you enable the policy retain their external IP addresses.
- This constraint accepts either an
allowedListor adeniedListbut not both in the same policy. - It is up to you or an administrator with the required permissions to manage and maintain the VM lifecycle and integrity. The constraint only verifies the VM's URI, and it does not prevent the VMs in the allowlist from being altered, deleted, or recreated.
Permissions needed for restricting external IP addresses
To set a constraint on either the project or the organization level, you must
have been granted the orgpolicy.policyAdmin role on the organization.
Set the policy constraint at the organization level
Console
- Go to the Organizational Policies page.
- If necessary, select the required organization from the project drop-down menu.
- Click Define allowed external IPs for VM instances.
- Click Edit to edit the external IP policy. If you can't access the Edit tool, you don't have the correct permissions.
Select Customize to set the org policy for specific VMs.
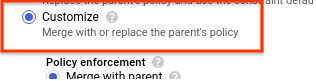
Select the required Policy enforcement and Policy type.
For Policy values, select Custom.
Enter a URI for a VM and press enter. The URI must be in the following format:
projects/PROJECT_ID/zones/ZONE/instances/VM_NAME
Click New policy value and enter URIs for VMs as needed.
Click Save to apply the constraint.
gcloud
To set a constraint for external IP access, you first need your organization
ID. You can find the organization ID by running the
organizations list command and
looking for the numeric ID in the response:
gcloud organizations list
The gcloud CLI returns a list of organizations in the following format:
DISPLAY_NAME ID example-organization1 29252605212 example-organization2 1234567890
Use the
gcloud resource-manager org-policies set-policy command
to set the policy. You need to provide your policy as a JSON file.
Create a JSON file in the following format:
{
"constraint": "constraints/compute.vmExternalIpAccess",
"listPolicy": {
"allowedValues": [
"projects/PROJECT_ID/zones/ZONE/instances/VM_NAME",
"projects/PROJECT_ID/zones/ZONE/instances/VM_NAME",
"projects/PROJECT_ID/zones/ZONE/instances/VM_NAME"
]
}
}
Replace the following:
PROJECT_ID: the project ID for this request, such asexample-project. Note that this is different than setting up organization policies, which require the organization numeric ID.ZONE: the zone of the VMVM_NAME: the name of the VM
Alternatively, you can specify a deniedValues list to indicate VMs that
you explicitly want to prohibit from having an external IP address.
Any VM not on the list would implicitly be allowed to have an
external IP address. You can only specify either allowedValues or
deniedValues but not both.
Then, pass in the file with your request:
gcloud resource-manager org-policies set-policy MY_POLICY.JSON --organization=ORGANIZATION_ID
Replace ORGANIZATION_ID with the numeric ID of the
organization.
If you don't want any VMs to have external IP access, you can set a policy
with allValues set to DENY:
{
"constraint": "constraints/compute.vmExternalIpAccess",
"listPolicy": {
"allValues": "DENY"
}
}
REST
Use the
setOrgPolicy() API
to define your constraint. The VMs in the allowedValue list you
specify are allowed to have external IP addresses. Alternatively, you can
specify a deniedValues list to express VMs that you explicitly
want to prohibit from having an external IP address. Any VM not on the
list would implicitly be allowed to have an external IP address. You can
only specify either allowedValues or deniedValues but not both.
For example, the following is a request to apply the
compute.vmExternalIpAccess constraint to an organization where VMs
from certain projects within the organization are allowed to have
external IP addresses:
POST https://cloudresourcemanager.googleapis.com/v1/organizations/ORGANIZATION_ID:setOrgPolicy
where ORGANIZATION_ID is the numeric ID of the
organization.
Now, in your request body, provide the policy for this constraint:
{
"policy": {
"constraint": "constraints/compute.vmExternalIpAccess",
"listPolicy": {
"allowedValues": [
"projects/PROJECT_ID/zones/ZONE/instances/VM_NAME",
"projects/PROJECT_ID/zones/ZONE/instances/VM_NAME",
"projects/PROJECT_ID/zones/ZONE/instances/VM_NAME"
]
}
}
}
If you don't want any VMs to have external IP access, you can set a
policy with allValues set to DENY:
{
"policy": {
"constraint": "constraints/compute.vmExternalIpAccess",
"listPolicy": {
"allValues": "DENY"
}
}
}Set the policy at the project level
Setting a policy at the project level overrides the policy at the organization
level. For example, if the organization level has example-vm-1 on the
allowedValues list but the policy at the project level has the same VM
on the deniedValues list, the VM wouldn't be allowed to have an
external IP address.
Console
Follow the same process documented under Set a policy constraint at the organization level but choose your project from the project selector instead of the organization.
gcloud
Use the
gcloud resource-manager org-policies set-policy command
to set the policy. You need to provide your policy as a JSON file. Create a
JSON file in the following format:
{
"constraint": "constraints/compute.vmExternalIpAccess",
"listPolicy": {
"allowedValues": [
"projects/PROJECT_ID/zones/ZONE/instances/VM_NAME"
]
}
}
Replace the following:
PROJECT_ID: the project ID for this request, such asexample-project. Note that this is different than setting up organization policies, which require the organization numeric ID.ZONE: the zone of the VM.VM_NAME: the name of the VM.
Alternatively, you can specify a deniedValues list of VMs that you
explicitly want to prohibit from having an external IP address. Any VM
not on the list would implicitly be allowed to have an external IP address.
You can only specify either allowedValues or deniedValues but not both.
Then, pass in the file with your request:
gcloud resource-manager org-policies set-policy MY_POLICY.JSON --project=example-project
REST
Use the
setOrgPolicy API
to define your constraint. The VMs in the allowedValue list you specify
are allowed to have external IP addresses. Alternatively, you can specify a
deniedValues list to express VMs that you explicitly want to prohibit from
having an external IP address. Any VM not on the list is implicitly
allowed to have an external IP address. You can only specify either
allowedValues or deniedValues but not both.
For example, the following is a request to set the
compute.vmExternalIpAccess constraint on a project to allow specific VMs
to have external IP addresses:
POST https://cloudresourcemanager.googleapis.com/v1/projects/PROJECT_ID:setOrgPolicy
Replace PROJECT_ID with the project ID for this
request.
The request body contains the policy for this constraint:
{
"policy": {
"constraint": "constraints/compute.vmExternalIpAccess",
"listPolicy": {
"allowedValues": [
"projects/PROJECT_ID/zones/ZONE/instances/VM_NAME"
]
}
}
}
Best practices for restricting external IP addresses
Avoid using the
deniedValueslist with this constraint. If you define values in thedeniedValueslist, it means that only the VMs in thedeniedValueslist are restricted from using external IP addresses. This could be a security concern if you want control over exactly which VMs can have external IP addresses. If you want to remove certain VMs from theallowedValueslist, update the existing policy to remove the VMs from theallowedListrather than putting the VMs into thedeniedValueslist at a lower hierarchy.If you want to set a policy over a large part of the resource hierarchy but exempt certain projects, restore the default policy by using the
setOrgPolicymethod by specifying therestoreDefaultobject to allow all VMs in the projects to be associated with external IP addresses. The current policies for projects are not affected by the default setting.Use the org policy together with IAM roles to better control your environment. This policy applies to only VMs but if you want to better control and restrict external IP addresses on network devices, you can grant the
compute.networkAdminrole to the appropriate parties.Any services and products that are running on Compute Engine within the organization or project with the policy enabled are subject to this org policy. Specifically, services such as Google Kubernetes Engine, Dataflow, Dataproc, and Cloud SQL are affected by this policy. If this is an issue, Google recommends that you set up other services and products in a different project that does not have the organization policy applied, and use Shared VPC, if needed.
Manage static external IP addresses
The following sections describe how to manage static external IP addresses for your VMs.
Determine if an internal IP address is ephemeral or static
Static and ephemeral internal IP addresses behave and appear the same in most contexts. However, with static internal IP addresses, you can use the same IP address for the same resource even if you delete and re-create the resource. In general, an ephemeral IP address is released if you stop or delete the resource.
To determine if an address is static or ephemeral, do the following:
In the Google Cloud console, go to the IP addresses page.
Find the address in the list and check the Type column for the type of IP address.
Unassign a static external IP address
Unassigning an IP address removes it from the resource but keeps the IP address reserved. After the IP address is unassigned, you can reassign the IP address to another resource.
You can also unassign the IPv4 or IPv6 address by deleting the VM.
Console
In the Google Cloud console, go to the IP addresses page.
Click External IP addresses.
Select the static IP address that you want to unassign.
Click Change to open the Attach IP address dialog.
From the Attach to drop-down list, select None.
Click OK.
gcloud
Check if a static IP address is in use by using the
gcloud compute addresses listcommand:gcloud compute addresses list
The output is similar to the following:
NAME REGION ADDRESS STATUS example-address-ipv4 REGION 198.51.100.1 RESERVED example-address-new-ipv4 REGION 203.0.113.1 IN_USE example-address-ipv6 REGION 2001:db8:1:1:1:1:1:1 RESERVED example-address-new-ipv6 REGION 2001:db8:4:4:4:4:4:4 IN_USE
- If the IP address is not in use, the status is
RESERVED. - If the IP address is in use, the status is
IN_USE.
- If the IP address is not in use, the status is
Retrieve the name of the VM that is using the IP address:
gcloud compute addresses describe ADDRESS_NAME \ --region=REGION
Replace the following:
ADDRESS_NAME: the name of the IPv6 address resource.REGION: the region of the IPv6 address resource.
The output is similar to the following:
address: IP_ADDRESS addressType: EXTERNAL ... region: https://www.googleapis.com/compute/v1/projects/PROJECT/regions/REGION selfLink: https://www.googleapis.com/compute/v1/projects/PROJECT/regions/REGION/addresses/ADDRESS_NAME status: IN_USE subnetwork: https://www.googleapis.com/compute/v1/projects/PROJECT/regions/REGION/subnetworks/SUBNET users: - https://www.googleapis.com/compute/v1/projects/PROJECT/zones/ZONE/instances/VM_NAME
The
usersfield displays the name of the VM that is using the IP address.Unassign the IP address from the VM.
To unassign an IPv4 address, delete the VM's access config file:
Get the name of the access config to delete. To get the name, use the
gcloud compute instances describecommand. ReplaceVM_NAMEwith the name of the VM.gcloud compute instances describe VM_NAME
The access config appears in the following format:
networkInterfaces: - accessConfigs: - kind: compute#accessConfig name: external-nat natIP: 203.0.113.1 type: ONE_TO_ONE_NATDelete the access config by using the
gcloud compute instances delete-access-configcommand:gcloud compute instances delete-access-config VM_NAME \ --access-config-name="ACCESS_CONFIG_NAME"
Replace the following:
VM_NAME: the name of the VM.ACCESS_CONFIG_NAME: the name of the access config to delete. Be sure to include the full name between quotes.
To unassign an IPv6 address range, use the
instance network-interfaces updatecommand:gcloud compute instances network-interfaces update VM_NAME \ --network-interface=nic0 \ --stack-type=IPV4_ONLY \ --zone=ZONE
Replace the following:
VM_NAME: the name of the VM that is using the IP address.ZONE: the zone of the VM.
Check that your static external IP address is now available and marked as
RESERVEDinstead ofIN_USE.gcloud compute addresses list \ --filter="ADDRESS_NAME AND region=REGION"
Replace the following:
ADDRESS_NAME: the name of the IP address resource.REGION: the region of the IP address resource.
Now that your static external IP address is available, you can choose to assign it to another VM.
REST
To unassign a static external IPv4 or IPv6 address, perform the following steps:
For IPv4 addresses, delete the access configuration attached to the VM that's using the address.
To check the access configuration details of a VM, make a
GETrequest to theinstances.getmethod.GET https://compute.googleapis.com/compute/v1/projects/PROJECT_ID/zones/ZONE/instances/VM_NAME
Delete the existing access configuration by making a
POSTrequest to theinstances.deleteAccessConfigmethod.POST https://compute.googleapis.com/compute/v1/projects/PROJECT_ID/zones/ZONE/instances/VM_NAME/deleteAccessConfig
Replace the following:
PROJECT_ID: the project ID for this requestZONE: the zone where the VM is locatedVM_NAME: the name of the VM
For IPv6 addresses, update the stack type of the network interface for the VM where the IPv6 address is attached.
Make a
PATCHrequest to theinstances.updateNetworkInterfacemethod.In the request body, update the value of the
stackTypefield toIPV4_ONLY.For example:
PATCH https://compute.googleapis.com/compute/v1/projects/PROJECT_ID/zones/ZONE/instances/VM_NAME/updateNetworkInterface { "networkInterfaces": [{ ... "stackType" : "IPV4_ONLY" ... }] }
Release a static external IP address
If you no longer need a static external IPv4 or IPv6 address, you can release the IP address by deleting the IP address resource. Deleting a VM does not automatically release a static external IP address. You must manually release static external IP addresses when you no longer require them.
To release a static external IP address, see Release a static external IP address in the VPC documentation.
What's next
- Learn more about IP addresses.
- Learn more about networks and firewalls.
- Learn how to address VMs using internal DNS.
- Review VPC pricing.
